You hear about hacks all the time. The news covers major websites who have had data leaks containing your email and password. Computers get infected and capture your login details for bank accounts and credit cards. In the worst cases, identity theft occurs because it is an easy crime to commit with a high reward.
In 2018, the passwords you used to trust to keep the bad guys out of your accounts are not enough anymore. Cyber attackers now use methods such as phishing, pharming, and keylogging to steal your password. Some have the power to test billions of password combinations.
If you’re like the majority of people, you use the same password for several websites. That means anybody who has figured out that password has access to everything you’ve logged into with it. In a time when it is extremely easy to look up what a person named their first pet or high school mascot, security questions aren’t much help.
Consider how a jewelry store operates. They don’t simply keep their valuables locked away with one key. There are alarms ready to be triggered, motion detectors, and sometimes even bars on the windows. Your data is valuable, just like jewelry. You need more than one line of defense to protect it.
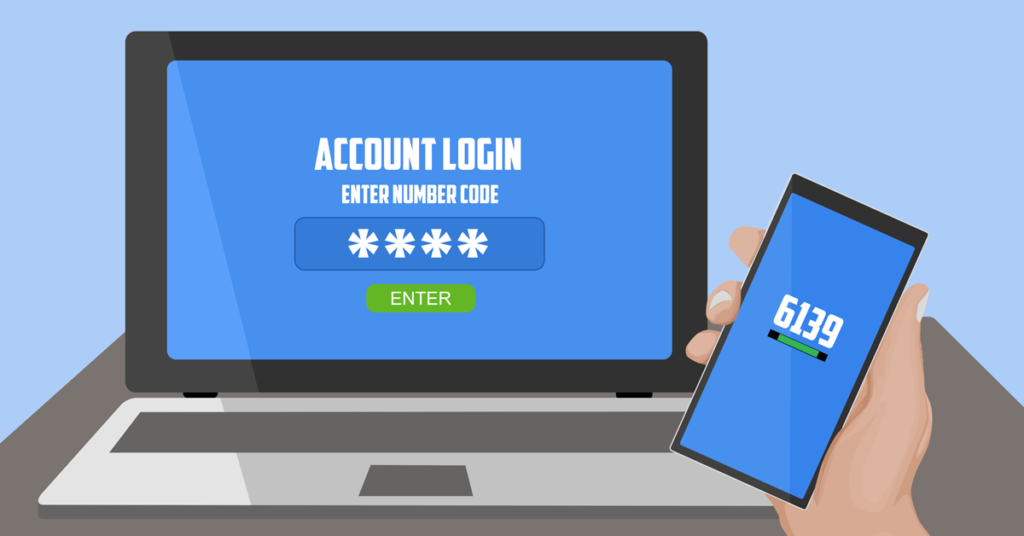
In the computer world, your second line of defense (after your username and password combination) is called “2-factor authentication.” Sometimes referred to as multiple-step or multi-factor verification, 2-factor authentication is a way to double check a person’s identity. This can be enabled every time a person logs in or just under certain circumstances. For example, signing in from a new device or different country might trigger 2-factor authentication.
Many of the services you may already use, such as Facebook, Gmail, Xero Accounting, and more, have 2-factor authentication options. If your bank has ever sent you a special code through text or email to enter before logging in, you’ve already used a type of 2-factor authentication. They can also be in the form of a smartphone app or a physical electronic dongle.
2-factor authentication is absolutely crucial for online banking, email, and online shopping such as Amazon or PayPal. It’s also a must-have for cloud storage accounts (like Dropbox or Sync), password managers, communications apps, and productivity apps. This is especially true if you frequently use the same passwords for different websites and apps.
Some may consider 2-factor authentication unnecessary for social networks, but these are actually very important to keep safe. For ease, a lot of websites and apps allow you to sign up through your Facebook or Twitter account. You need to keep these networks safe so that somebody with your password can’t suddenly get into every account you have linked.
The point of using 2-factor authentication is to make hackers’ lives harder and prevent them from getting into your accounts. If they have captured your login username and password, they still need a second device to get in, especially when the computer or phone they are using has never logged into your account before. This makes it significantly more difficult for anybody to breach your account.
Plus, if you receive a notification with a special code to enter for logging in, and you weren’t trying to log into that account, you have a good signal that somebody else was trying to get in. That means it’s time to change that password and be grateful you had 2-factor authentication.
It’s unfortunate that there is currently an abundance of skilled hackers ready to take advantage of those unprepared. Luckily, you can still stop them -even if they have your login information at hand. 2-factor authentication is one of the easiest methods to keep your accounts safe.
Give us a call at (312) 600-8357 to help secure your business and accounts.










